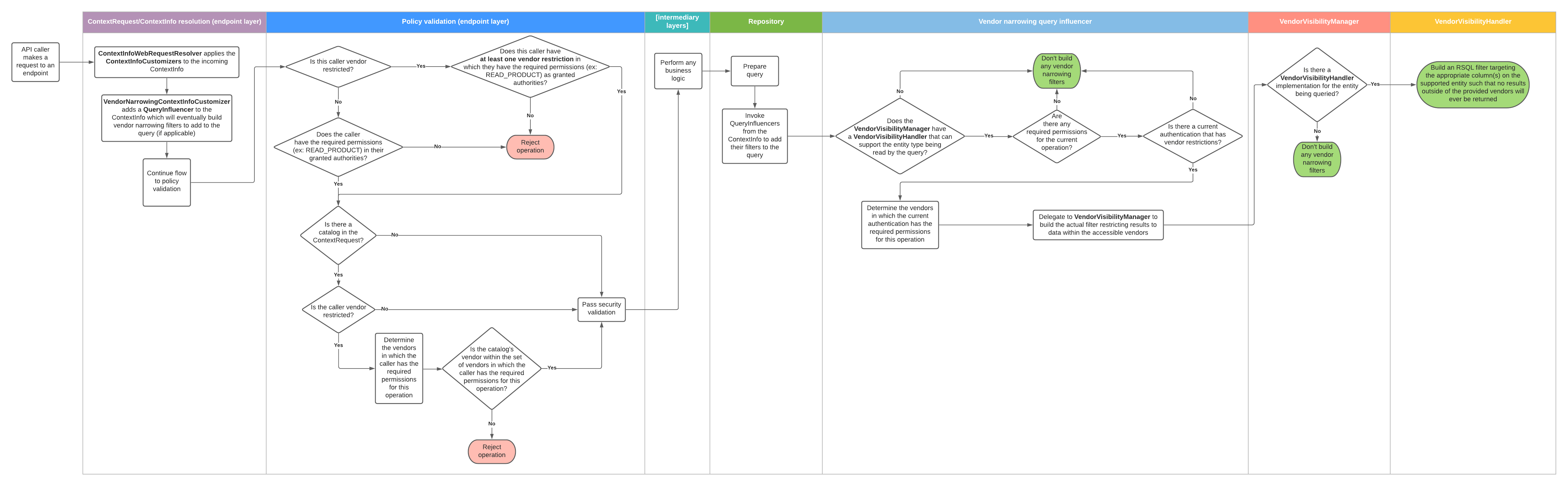
Consider a multi-vendor admin user which has the READ_PRODUCT authority in vendorA, and has the [READ_PRODUCT, UPDATE_PRODUCT] authorities in vendorB.
If this user were to try to read a page of products, the policy validation would pass since the user has the required READ_PRODUCT authority in at least one of their vendor restrictions.
Then, the narrowing logic would see that the user has the READ_PRODUCT authority in both vendorA and vendorB, and would build a filter allowing products from both vendors to appear in the results.
Now let’s say the user tries to make a request to update some productA that happens to be in vendorA.
The policy validation will again pass, since the user has UPDATE_PRODUCT in at least one of their vendor restrictions (vendorB).
The narrowing logic will see that the user has UPDATE_PRODUCT only in vendorB, and will build a filter only allowing products from vendorB to appear in the results.
This will mean that when the query for productA runs, it will simply not be found and the update will fail.